Please enjoy the first chapter of “The Little Book of Local Government Fraud” by Charles Hall, CPA. An fun-to-read and informative self-study course available at Yellowbook-CPE.com.
Objectives:
- Identify common characteristics of fraudsters
- Identify various types of fraud schemes
Before we dig into fraud at the ground level of individual transactions, let’s take a look at local government fraud from 30,000 feet. We need to understand the big picture before drilling deeper—at the transaction level—where fraud really happens. To initially develop our understanding of governmental fraud, let’s examine:
- Who steals
- The language of fraud
- Where fraud occurs
- How and why fraud occurs
Thou Shalt Not Steal
I learned it in Sunday school: Thou shalt not steal. I knew better, but the temptation of taking one of my father’s five-dollar bills was too great. Besides, he’d never know—he had so many five-dollar bills. My little mind rationalized, “He won’t even miss it.” And surely, I, a five-year old, needed the money more than my father. So, I took and hid, as so many throughout history have done (Al Capone, Bonnie and Clyde, and now, freckled-faced South Georgia boy Charles Hall).
My secret hiding place was a red stamp box in the hallway of our home. My father must have found it. On the way to our Florida vacation, he asked, “Who took five dollars from my billfold?” First silence filled the air…then my sister chimed in, “Not me,” and in rapid staccato fashion, my two brothers yelled “Not me either.” Hoping to hide my guilt, I quickly retorted “Not me” and glanced around the car as if to say, “Who could have done this?”
It was then I had the most vexing vacation of my life. I couldn’t tell my father. Like Ralphie from A Christmas Story, I imagined my Dad would kill me. It was only upon arriving back home that I confessed, and my father swept me up in his arms saying, “Son, I knew it was you all along.” (Thankfully, he did not kill me.) As a kid, I learned my lesson. Some adults never do. So, what does a typical fraudster look like?
The Poster Child
Through the years, I’ve seen people from diverse social, ethnic, and age groups steal. Even so, fraud studies point to one consistent picture of the typical fraudster. And what is that picture? He looks like me. He’s male, educated, in a position of authority, and has been on the payroll for a while.
The Association of Certified Fraud Examiners (ACFE), in its 2018 Report to the Nations (a fraud survey), indicates the following about those who steal:
- 69% of frauds are committed by males.
- The median fraud loss from males is $156,000; the median loss from females is $89,000.
- Approximately 53% of all fraudsters are between the ages of 31 and 45; fraud losses tend to rise with the age of the perpetrator.
- Approximately 44% of fraudsters have between one and five years of tenure at their organizations; fewer than 10% of perpetrators commit fraud within the first year on the job.
- 61% of fraudsters have a college degree or higher.
- Fraud schemes committed by owners/executives cause the largest median losses ($850,000).
My observation is that there is greater diversity in governments, so the above statistics may not be as relevant. Rather than trying to identify fraudsters by typical characteristics (e.g., gender or education), I like to consider:
- Who are the trusted employees with authority?
- What can they do?
- Who fully understands the accounting system?
A fraudster is frequently the person you would not expect to steal: the trusted employee, the individual who has been around the longest, the one who understands and controls accounting (remember Rita Crundwell). The trusted, long- time staff member is usually accorded greater control— because he or she is seen as trustworthy. This person has the keys to the kingdom.
Additionally, I’ve noticed that elected officials fit this “trusted” category, and some take advantage of the power they possess to circumvent internal controls. For example, who is going to question the sheriff? When one person—regardless of who he or she is—has full control of the accounting process, be careful!
So why is the trusted employee the one who commonly steals?
Because he can.
You may be thinking: Duh? But this is a critical point. As we will soon see, this dynamic—referred to as opportunity—is a key component of fraud.
While in France
Once while I was traveling in France, I was looking for a train station. I stopped a kind elderly gentleman on the street and asked, in English, for directions. I soon realized we were not understanding one another. In my frustration, I began to say, “toot, toot!” He smiled (thinking “crazy American”) and pointed; soon I reached my destination. In this instance, I was able to overcome the language barrier. But to make our fraud journey easier, we need a common language. So please allow me to define the following terms:
- Fraud
- Abuse
- Asset misappropriation
- Corruption
- Financial statement fraud
- Fraud prevention
- Fraud detection
Fraud – What Is It?
I recently read of a southern city that had undocumented expenses of $200 million over a twelve-year period. Is this fraud? Not necessarily. In this instance, you need to demonstrate that funds were stolen before you can prove fraud. Though a red flag, the lack of invoice support does not prove that theft occurred.
In another example, Bobby Johnson, the CFO of a hospital authority, recently changed the method of calculating the allowance for uncollectible accounts. The change resulted in a positive change in net income of $1.2 million dollars. Is this fraudulent reporting? It all depends. Governments can and sometimes should change how they compute estimates. Did Bobby change the computation to juice up net income? Or does the change more accurately reflect the hospital authority’s environment? It’s not always easy to know. But remember this: to prove fraud, you must prove intent. If Bobby did not intend to misrepresent the numbers, fraud does not exist. An error in judgment? Possibly, but no fraud.
The Association of Certified Fraud Examiners defines occupational fraud as: “The use of one’s occupation for personal enrichment through the deliberate misuse or misapplication of the employing organization’s resources or assets.”
I define fraud as:
- Money is stolen, or
- Financial statements are intentionally misstated (also known as “cooking the books”)
Three Fraud Categories
The ACFE categorizes fraud as follows:
- Asset misappropriation schemes: An employee steals or misuses the organization’s resources (e.g., theft of company cash, false billing schemes, or inflated expense reports)
- Corruption schemes: An employee misuses his or her influence in a business transaction in a way that violates his or her duty to the employer in order to gain a direct or indirect benefit (e.g., schemes involving bribery or conflicts of interest)
- Financial statement fraud schemes: An employee intentionally causes a misstatement or omission of material information in the organization’s financial reports (e.g., intentionally recording fictitious revenues or understating expenses)
Abuse – What Is It?
Another closely related term is abuse. Think of abuse as a lesser form of fraud, though the distinction between the two can sometimes blur.
Examples of abuse include:
- Employees calling in sick when they are well
- Employees driving public vehicles for personal purposes
- Employees making excessive personal phone calls during work hours
- Employees taking government-owned equipment home for personal use
- Employees using the government’s copy machines for personal projects or businesses
This book mainly deals with fraud rather than abuse; nevertheless, consider that both occur, and that you may need to craft abuse-related preventive policies in addition to your fraud prevention measures.
Fraud Prevention and Detection
Fraud-related internal controls are commonly broken down into two categories:
- Fraud prevention
- Fraud detection
Prevention is usually the more costly of the two, but it is more effective. As the name states, these procedures are designed to stop fraud before it occurs. An example of a prevention procedure is the review of direct deposit bank account numbers for potential duplicates prior to payroll processing.
By contrast, detection measures are performed after trans- actions are processed (and after fraud may have taken place). As you might expect, these controls tend to be less expensive and less cumbersome to administer. An example of a detection procedure is the review of W-2s at year-end for excessive payments.
We’ve now defined our fraud terms, so let’s examine the nature of fraud. What types of theft are most common? How long do most schemes last? What are the ingredients of fraud?
Which Fraud Is More Common?
Theft is the most common type of fraud in governments. Money can be stolen directly (e.g., skimming) or indirectly (e.g., bribery). Funds can be stolen by those with direct access to cash (e.g., a receipting clerk) and by those without direct access to cash (e.g., elected officials).
Financial statement fraud is not common in most local governments. Are there misstatements? Yes. Are the mis- statements intentional? Usually no. The misstatements are normally mistakes rather than manipulation. Public sector entities simply have fewer incentives to manipulate the financial statements than their private-sector counterparts. For instance, a publicly-held company may manipulate profits in order to increase stock prices, but public entities don’t have this temptation.
Incentives for manipulating governmental financial statements do increase as public entities grow in size. Complex investment and debt agreements can tempt governments to manipulate numbers, especially when financial conditions have deteriorated. Complexity (e.g., interest rate swaps) may provide enough opacity to hide the nonrecognition of adverse financial events. And governments with debt may have certain financial statement requirements known as debt covenants that increase the temptation to cheat on the numbers. Though auditors should consider the possibility of financial statement fraud, this book focuses primarily on the more prevalent forms of governmental fraud: asset misappropriation and corruption.
Average Local Government Fraud Damages
The ACFE’s biennial fraud survey usually reports median governmental per-case damages in the range of $100,000 to $120,000, but fraud committed by upper-level management can easily exceed $1 million depending on the size of the government. As we saw in the Rita Crundwell story, Dixon, Illinois, a city of just 16,000, was defrauded of over $53 million.
Given that the 2012 Census of Governments identifies approximately 89,000 U.S. local governments, there are a great number of counties, cities, towns, school districts, and special districts where fraud can occur.
Average Life of a Fraud
In the beginning of my career, I naively believed that fraud was instantaneously detected as it occurred—surely within a month’s time. But the ACFE’s fraud survey consistently shows that frauds have a life of about eighteen months before detection. Bear in mind this statistic reflects fraud cases where theft has been detected; unknown frauds are not included in the computation. Some local government frauds exist for decades without detection.
Fraud – Where It Happens
The 2018 ACFE’s Report to the Nations found that governments are the second most commonly victimized industry (trailing only banking and financial services). And within governments, the 2018 survey reflects the following concentrations of fraud schemes[1]:
| Scheme | Percent of Cases |
| Corruption | 50% |
| Billing | 15% |
| Noncash | 22% |
| Skimming | 11% |
| Payroll | 7% |
| Check Tampering | 9% |
| Cash on Hand | 11% |
| Cash Larceny | 11% |
| Financial Statement Fraud | 5% |
| RegisterDisbursement | 2% |
In the following pages, we will focus on the areas that open the door to the greatest potential damage in your government. Expense reimbursement fraud, for example, is common but usually involves less dollar damage than corruption. So, we will spend more time examining corruption and other areas where the threat of loss is greatest.
Stealing from Little Old Ladies
Many who steal from local governments view their theft as taking from the government itself. But from whom is the fraudster ultimately stealing? The local citizens—from Mr. Johnson, the owner of the local feed and seed; Mrs. Durham, the pastor’s wife; Lloyd Tailor, a cotton farmer; and Rez Jacobs, the postmaster. These people pay property taxes, water fees, and all the other sources of money that flow into the local government. The fraudster is stealing from his next-door neighbor, from those he goes to church with, from members of the local Lions Club, and from volunteer firefighters.
Those who steal from local governments tell themselves things like, “The city doesn’t need this money, and besides, it’s the government.” Stealing, at least psychologically, is easier if the thief sees himself as taking from a cold sterile entity rather than from his neighbors. Taking from the government is easier than pilfering from the little old ladies down at the local senior citizens’ center, though this is exactly what is occurring. You may, at this point, be thinking, “Only callous people would do such a thing.” Well, let’s see.
Stealing While Dying
In one of the strangest frauds I’ve seen, the bookkeeper was stealing money while dying. Going to meet your Maker with the fresh scent of theft on your hands is not a good way to go.
I had provided external audit services to this health department for years and knew the bookkeeper (we’ll call her Katie) quite well. She sent me thank you cards—yes, thank you cards—for my audit work. Katie was polite, well spoken, and great at her job. If ever I thought there was someone who would not (and could not) steal, it was—you guessed it—Katie. But external circumstances can make even the best people do the improbable. During the course of one audit year, Katie developed cancer. The medical treatments resulted in numerous medical bills, many of which she received while still working off and on. Sadly, she eventually died.
Knowing that Katie had passed away, I knew the audit would be challenging, especially since the health department board had not hired anyone to replace her. Upon my arrival I requested the bank statements, but the remaining employees could not locate them (not a good sign). I thought maybe she had taken the bank statements home and had not returned them due to her illness. Her family members said no. After the employees had searched for some time with no result, the health department requisitioned the bank statements and cleared checks from the bank.
In reviewing the cleared checks, I quickly noticed round-dollar vendor checks written to Katie. The first one was for $7,000. My first thought was, “Not Katie. I’ve known her too long. No way. Surely an explanation exists.” But there was another, and another…
Reporting the theft to the health department board was difficult. Here was an honest person who had stolen money because she felt she had to.
This is one case where I wanted to just let it go, to walk away and pretend it didn’t happen. But I knew that was not an option. Can you imagine being the board member that called Katie’s husband—just months after her death—and informed him of the theft? Fraud is an ugly thing.
If you’re an auditor and you need a reason to communicate internal control weaknesses in an open manner, here’s one—for the employee’s own safety (not to mention your own). Sometimes money is too tempting, even for the best of people.
The Fraud Triangle
Fraud experts commonly explain fraud using the three elements of the fraud triangle:
- Rationalization (Katie’s unselfish desire to leave her family with no medical bills)
- Incentive (need for cash to pay medical bills)
- Opportunity (almost no segregation of duties)
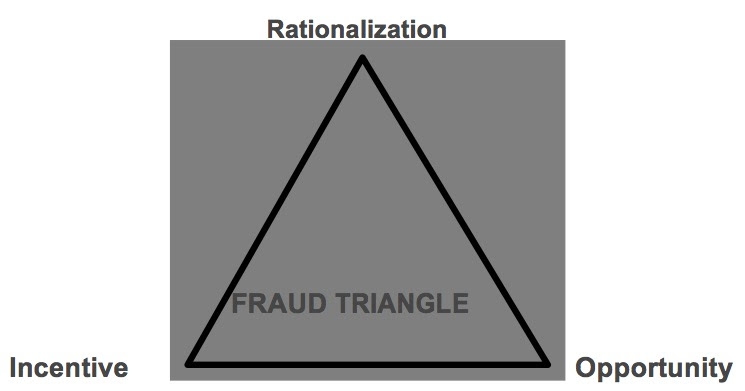
Katie was authorized to sign checks. Though the checks required two signatures, the bank cleared the checks with just Katie’s signature. Since Katie keyed all transactions into the computer and reconciled the bank statements, she had the keys to the castle. We call this opportunity.
The people you’re auditing are too honest to steal? Maybe. Or possibly you’ve worked side by side with governmental employees and you believe them to be saints. Maybe. We don’t know about their personal lives—or what will happen in the future. Fraud percolates in these unshareable problem areas such as financial stress, gambling debts, affairs, or simply a desire to keep up with the Joneses. When it comes to designing accounting systems, we need to largely disregard the character of people working in the government and design the system as if fraud may happen.
Lesson Learned
- When records go missing—pay attention
- When you see round-dollar vendor checks—dig deeper
- When your government lacks segregation of duties— raise your antenna
While all three elements of the fraud triangle are important, in the following pages we will focus primarily upon opportunity. Of the three, opportunity is the part we can, at least to some degree, control. Governments are seldom able to manage a fraudster’s incentive or rationalization. Incentive usually develops independent of the fraudster’s employment; think of the medical bills, for example. The fraudster, prompted by the incentive, first calms his conscience by rationalizing. Next, he exploits the opportunity (control weakness). If we can close the door to opportunity, fraud will be greatly diminished and possibly eliminated.

 Yellowbook-CPE.com is registered with the National Association of State Boards of Accountancy (NASBA) as a sponsor of continuing professional education on the National Registry of CPE Sponsors. State boards of accountancy have final authority on the acceptance of individual courses for CPE credit. Complaints regarding registered sponsors may be submitted to the National Registry of CPE Sponsors through its website:
Yellowbook-CPE.com is registered with the National Association of State Boards of Accountancy (NASBA) as a sponsor of continuing professional education on the National Registry of CPE Sponsors. State boards of accountancy have final authority on the acceptance of individual courses for CPE credit. Complaints regarding registered sponsors may be submitted to the National Registry of CPE Sponsors through its website: