In this episode of THE SAMPLE, Leita Hart-Fanta, CPA discusses how to fight the bureaucracy.
green book
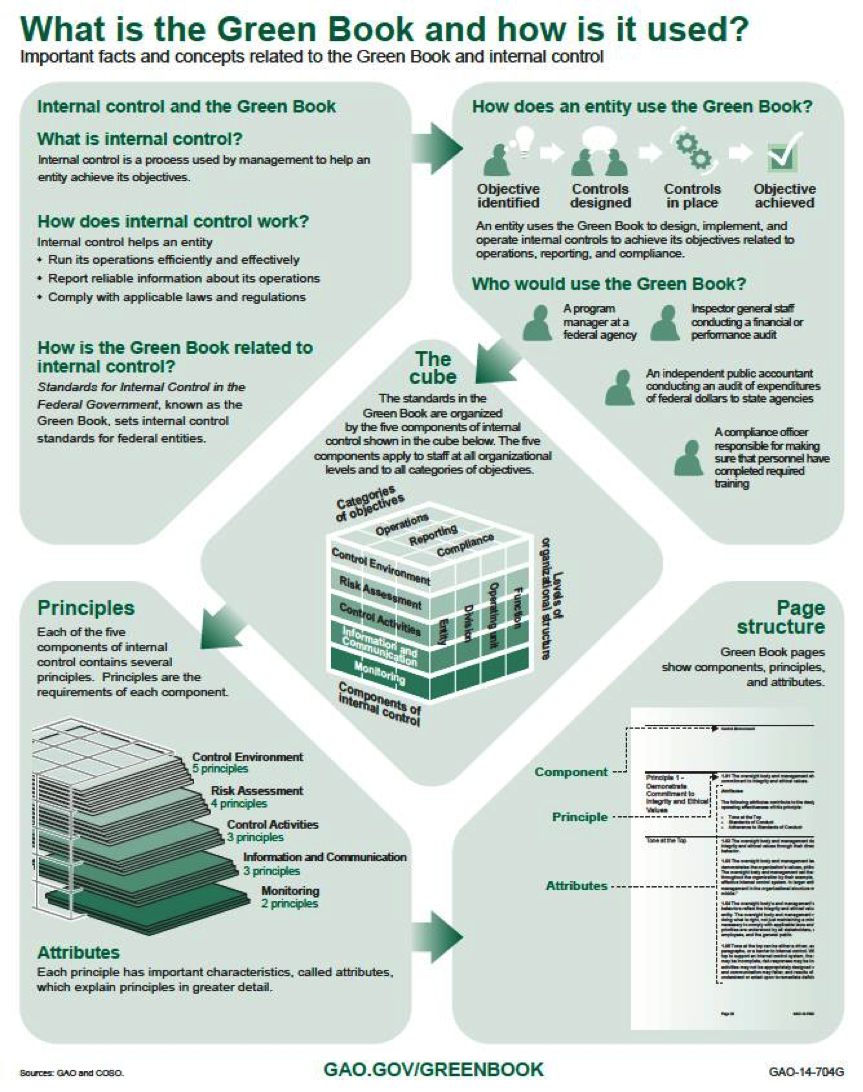
What Is the GAO Green Book?
In this episode of THE SAMPLE, Leita Hart-Fanta, CPA answers the question, “What is the GAO’s Green Book?” The Green Book’s formal title is Standards for Internal Control in the Federal Government and is a close copy of the COSO model.
Blending the Green Book with the Yellow Book
Objectives: Identify the purpose of the GAO’s Green Book. Distinguish between components of internal control. Distinguish between management objectives Choose a finite subject matter on which to apply controls Identify the auditor’s responsibilities regarding application of the Green Book Most of the changes between the 2011 Yellow Book and the 2018 Yellow Book that we […]
The Most Important Change to the Yellow Book is the Green Book
I’ve had a few months to digest the changes to the 2018 Yellow Book (Government Auditing Standards),and I’ve taught a few seminars and webinars about the changes. Most of the changes do not shock my audiences. But I am noticing that quite a few auditors are not familiar with the Green Book which was published by […]
Pulling It All Together
What’s the matter with the crowd I’m seeing? “Don’t you know that they’re out of touch?” Should I try to be a straight-A student? “If you are then you think too much. Don’t you know about the new fashion, honey? All you need are looks and a whole lot of money?” It’s the next phase, […]
Fraud Risk per the GAO’s Green Book
Just because you’re unaware of the risk, doesn’t mean it isn’t there Just because you aren’t conscious of something dangerous, doesn’t mean it isn’t lurking. One of the most important themes of the GAO’s Green Book (and the 2013 COSO model it is sourced from) is consciousness. Instead of just playing along with the crowd […]




 Yellowbook-CPE.com is registered with the National Association of State Boards of Accountancy (NASBA) as a sponsor of continuing professional education on the National Registry of CPE Sponsors. State boards of accountancy have final authority on the acceptance of individual courses for CPE credit. Complaints regarding registered sponsors may be submitted to the National Registry of CPE Sponsors through its website:
Yellowbook-CPE.com is registered with the National Association of State Boards of Accountancy (NASBA) as a sponsor of continuing professional education on the National Registry of CPE Sponsors. State boards of accountancy have final authority on the acceptance of individual courses for CPE credit. Complaints regarding registered sponsors may be submitted to the National Registry of CPE Sponsors through its website: